SEX IS GOOD. But as with all things, sex also has its "dark side". If you are not careful, you can get hurt.
ROAM IS GOOD. I am a firm believer in Roam's vision. But as with all things...
This article is about information security. While I will focus my discussion on roamresearch.com, my points are broadly relevant in today's online/digital world.
My goal with this post is not to freak you out, but to scare you just enough, so that you seriously consider what information you keep in your graph (or in the cloud, on your phone, on your PC), what extensions you install, and which graphs (and websites...) you visit.
A world without evil would be great. We would not need to spend money on locks, fences, military, police, etc. Our life would be simpler because we would not need password managers, two-factor authentication, pin codes, or encryptions. We would not have to carry around keys. We could ride our bike without needing to haul around a large lock... you get my point.
Unfortunately, the world is not without evil. There are people and organizations whose sole job is to find and exploit vulnerabilities, to cause you harm. Information security is a genuine issue. Not understanding the risks and acting as if those risks did not exist is playing Russian roulette. Most people don't get hurt, but those that do, regret not taking action upfront.
Disclaimer
I am just a layperson who likes to research topics on the internet. I don't have an information security certification like CEH (Certified Ethical Hacker), CISSP (Certified Information Security Professional), CISM (Certified Information Security Manager), CISA (Certified Information Security Auditor), etc. While I am pretty confident that most of what I am sharing is in line with best practice, take my advice with a grain of salt, and always do your own research, never blindly follow my advice.
Fear-Setting
I took the term "Fear-Setting" from Tim Ferris (Fear-Setting: The Most Valuable Exercise I Do Every Month)
It is essential to consider worst-case outcomes, assess their impact, think through what we would do should they happen, and what we can do today to mitigate them.
Without striving for completeness, here are the top three worst-case outcomes I could think of.
Identity theft
Someone uses your private journal and other information in Roam to forge an identity, then uses this to access your bank account. In a worst-case scenario, this could lead to the complete loss of your savings. This risk, of course, is also very relevant for all the information you voluntarily share about yourself on Twitter, Facebook, your blog, and other social media. You need to be aware of this risk and be mindful of what you write in Roam and what you post on social media.
Leakage of confidential information
Imagine your research, your business transactions, or your private journal getting in the wrong hands. The information could be used to blackmail you or to plot a broader attack against you or your company. In research, it could cost you your grant, or worst.
I don't think I am exaggerating. Read this article about Drop Smack, which exploited a DropBox vulnerability to penetrate corporate networks: DropSmack: How cloud synchronization services render your corporate firewall worthless
Loss of work/intellectual property
This scenario does not involve an attacker. Think of losing information because of a bug, or because Roam Research goes out of business, or because you do something silly, that destroys your graph. What if you don't have a backup? What if you have a backup, but there is no service to load it into? Depending on your use of Roam, such an incident could set you back many months.
Aspects of information security.
When thinking about information security, it is helpful to consider the following three aspects. If you are interested to learn more, there are many resources on the internet. I borrowed the below definitions from this article: The three pillars of cybersecurity.
Confidentiality
The purpose of ‘Confidentiality’ is to ensure the protection of data by preventing the unauthorized disclosure of information. Only individuals with the legitimate authority to access the required information should be permitted it, also known as permissions on the “need to know” basis. At large, the goal of confidentiality is to stop sensitive data from getting into the wrong hands.
With Roam, this means that you want to maintain the privacy of your private graph.
Integrity
This principle focuses on the accuracy, trustworthiness, and validity of information throughout its life-cycle. Information only holds its value if it’s truthful, therefore effective measures need to be taken to prohibit the alteration of data whether at rest or in transit by unauthorized individuals or processes.
Some of you may recall my tweet from the end of February. It was about how I almost lost all my data in Roam when a script I was developing went rogue during testing.
What was spooky about that incident is how only a day later I noticed the widespread damage in my database... certain blocks were missing, pages wouldn't load. It was a typical case of an integrity issue. I thought I had my database intact, but when I wanted to access information, it was no longer there or was incomplete/faulty. Imagine if I only realized that an important piece of information went missing a year later when I have already discarded my backups. I was lucky that the impact was so widespread and so immediate that I noticed the issues within a day.
Availability
Availability refers to information being accessible to authorized parties as and when it is needed.
For Roam, this means that servers are up and running, that you have backups of your data, that your network connection is working, etc.
The good news
To understand how Roam performs from a security standpoint I ran a few tests using free web-security audit tools, following guidance in these articles: 12 Online Free Tools to Scan Website Security Vulnerabilities & Malware and 13 tools for checking the security risk of open-source dependencies.
Roam got overall good scores on these tests. This means that the security certificates, message headers, cookies, external content, etc. seem to be in good order, with only minor issues highlighted by the scanner. Well done, Roam!
Threat scenarios
Attack surface, attack vectors
The attack surface of a software environment is the sum of the different points (for "attack vectors") where an unauthorized user (the "attacker") can try to enter data to or extract data from an environment. Keeping the attack surface as small as possible is a basic security measure. (Attack surface - Wikipedia)
There are many attack vectors and breach methods that hackers can use. Here are the ones I believe are most relevant to Roam.
Malicious or poorly written extensions
There are many ways to extend Roam, and frankly, this flexibility is part of what makes Roam so compelling to me. An attacker could use all of the current ways of extending Roam for malicious purposes. These include roam/js plugins, roam/render components, browser extensions, and yes, even roam/css style sheets.
The first three did not surprise me, Roam itself (or your browser in case of extensions) warns us about these risks.
The widespread use of open-source libraries exacerbates the risk. These are extremely hard to track down. The enthusiastic Roam hacker community does not have the skills or resources to validate all the libraries used. If you doubt my assessment on the use of open-source libraries, I recommend reading this article: 13 tools for checking the security risk of open-source dependencies. This sentence summarizes the article well: The biggest problem is that organizations still believe that open source code is more secure than commercial code.
I was, however, surprised to learn about the attack surface posed by CSS code. This article, about a CSS-based "keylogger", was an eyeopener to me: CSS Steals Your Web Data. In a nutshell, the idea is to use conditional formatting based on content on the webpage to load different remote graphical components (e.g. icons) and to use these remote load requests as a signaling system to communicate about content on the page. The use case mentioned in the article concerns stealing pin codes using this approach.
Of all the risks covered in my article, extensions pose by far the biggest risk.
So what can you do? Avoid "promiscuity". Minimize the number of extensions you use, and use plugins / components / extensions / css from trusted sources only. It is good practice to read through the code before you enable it, or if you don't have the expertise, then ask someone to do it for you.
The good news is, Roam is working on a plugin depot which hopefully will feature some level of auditing of code by Roam.
Compromised credentials/authentication
Roam offers two types of authentications. Federated authentication with a Google account and username and password-based authentication.
The default password policy mandated by Roam is six characters, which is far, far, far too weak. The title of this article is very telling: Use an 8-char Windows NTLM password? Don't. Every single one can be cracked in under 2.5hrs.
Depending on the maximum password allowed by platforms, I prefer to use 20+ character long random passwords containing letters, numbers, and special characters. If you think this is too much, please make your passwords at least 10 characters long, containing lowercase and uppercase characters and numbers.
Federated Google authentication is the safer option, especially if you use Google's two-factor authentication - which you should!
Intercepted network traffic
An example of this threat would be a Man-in-the-middle attack. In such an attack, a party in the middle intercepts the traffic between your PC, potentially reading or altering the content. This is the type of scenario why you should always avoid free Wi-Fi hotspots, and never, NEVER do any online banking through such connections.
Considering the overwhelmingly positive rating by the web scanners shown above, I believe the risk of a man in the middle type of attack is very low for Roam.
An attack on Roam servers
I don't know where and how Roam is hosting its servers. Based on the use of firebase storage, I assume that they host the entire service on Google's infrastructure. If this is the case, and Roam is on Google Firebase, then the risk of out-of-date security patches, missing virus scanners, inadequate logging, etc. is probably low.
Access to documents and images you have uploaded to Firebase storage
Roam offers unlimited storage for your uploaded content on Firebase Storage. This is very convenient!
The risk with the current implementation is that you have no way of deleting files. In addition, the links in your database include the authorization token for each file, thus anyone with access to your graph (or the link) will have access to the file. Even if you are aware of the security implications of storing data on Firebase, it may happen that you upload something by mistake - imagine dragging the wrong file from a folder, and not being able to undo your action.
If you are concerned about Firebase, I recommend using a paid cloud storage alternative. I use OneDrive. I have even created get-my.link a while back as a convenient way to create embeddable OneDrive links for the various applications I use(d). As an alternative to OneDrive, storing files on Google Drive has the benefit that you may embed resources such as Google Sheets into your Roam graph, such that you can immediately edit their content, without needing to open the file in a separate window.
What can you do about these risks?
As a rule of thumb, you have four options for dealing with risk.
Accepting it means you understand the risk, you have considered the worst-case outcomes, and you have decided to live with the risk as the benefits outweigh it.
Avoiding it means you understand the risk, you have considered the worst-case outcomes, and you have decided to find another way, by either not doing the activity altogether or doing it in a completely different way, such that the risk does not materialize (i.e. use a paper-based diary instead of an online journal).
Buying insurance is a way to transfer the risk. I doubt this is a relevant scenario in our case.
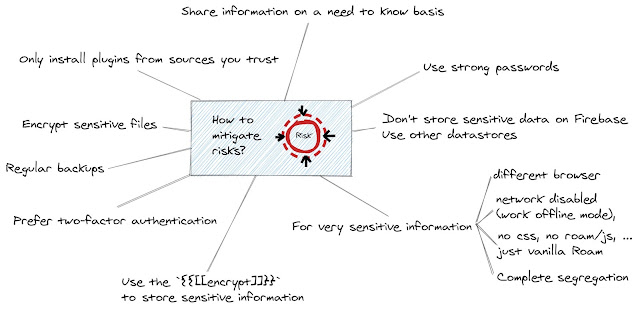
Reducing it means you reduce the attack surface, by following the advice above and the few additional ideas below.
- Share information (access to your graph) with others on a strict need-to-know basis.
- Only install plugins from sources you trust. Even with these, I would recommend minimizing the exposure surface by installing the truly essential stuff only.
- Prefer two-factor authentication over username/password.
- Don't store sensitive data on Firebase. Use other file-stores, such as OneDrive, iCloud, Google Drive, Box, DropBox, etc. Encrypt sensitive files in a password-protected archive, using a strong password (20+ characters, lower+upper case, number, special characters).
- Use the
{{encrypt}}control in Roam to encrypt sensitive information in your graph. - I would not recommend storing very sensitive information in Roam. If you have no other option, then use a different browser for the sensitive graph (e.g. if you normally use Chrome, run the sensitive graph in Firefox). Even better if you use a different physical computer. Don't use extensions other than those that you have created for yourself (assuming you have used no open source components). Keep the two environments separate, i.e. never open other graphs in your "safe" browser and vice versa.
Conclusion
I continue to believe in the Roam vision. My recommendation is to adopt the "reduce" response approach to the above risks.
Reduce the risk by being more selective about the graphs you visit and the extensions you install. You can further reduce the risk by using a cloud storage service for your files, that allows proper deletion and modification of files.
Consider the information you keep in Roam. If there is something very sensitive, I recommend taking the "avoid" approach for now. Keep your sensitive data safe!









great content/article Zsolt! So may are using Roam as a CRM system which I was considering as well, but to have client info such as email, phone and addresses would probably not be a good idea? Best - M
ReplyDeleteI agree, Roam is ideal as a personal or small business CRM system, and yes, information security is crucial when dealing with 3rd party personal data. Should you decide to continue with your CRM in Roam, you can mitigate some of the risks by placing sensitive customer data into {{encrypt}} blocks. Keep in mind however, that there are attack vectors that could allow an intruder to access text as you type... but if you are careful with what multi-player graphs you visit and what roam/js and browser plugins you use, the risk can be minimized.
Delete